Introduction
Problem
The next billion users who will enter Web3 will have difficulty entering without the empowerment of social accounts. The Web3 ecosystem needs Web2 functionality that keeps the onboarding processes smoothly and seamlessly.
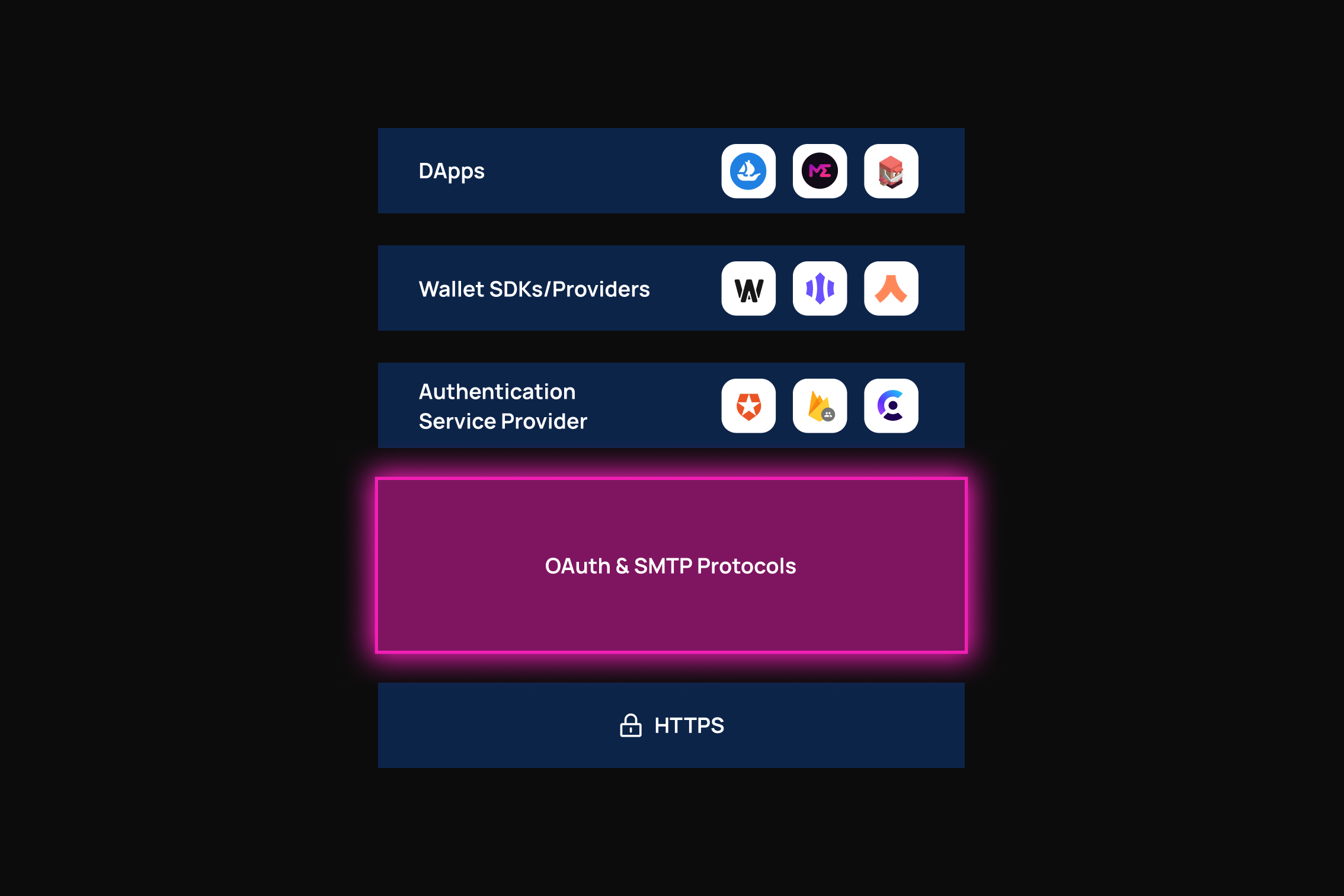
Identity authentication is fundamentally a process where users are required to prove their identity to challengers. Traditional Web2-style authentication methods such as Email-OTP and OAuth have a single centralized witness, which leads to three main issues:
Centralization: The result of this witness cannot be re-verified by anyone else, which forces users to trust the verifier/service provider.
Permissioned: Centralized identity authentication gives service providers the ability to cease services for a user, posing a Single Point of Failure (SPOF) risk.
Privacy Concerns: Users' Web2 and Web3 accounts become linked.
What is DAuth Network?
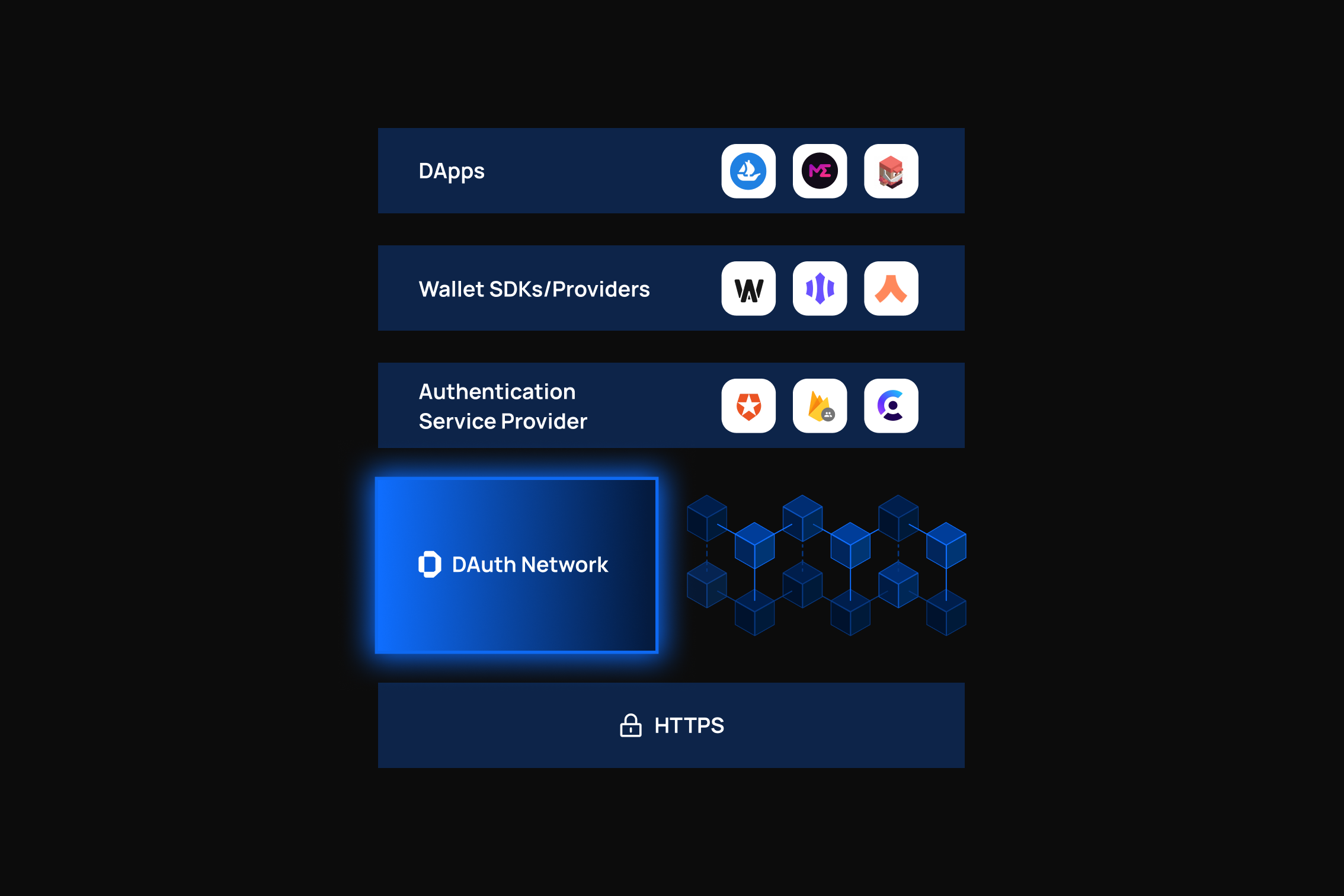
DAuth acts as a decentralized and permissionless witness participating in the authentication of the user's Web2 identity. The result of DAuth's witnessing will generate a proof in real-time, which can be verified by anyone, thus achieving the characteristics of decentralization. At the same time, the DAuth protocol ensures that no user information is visible during the witnessing process, ensuring the anonymity of the user's identity.
What makes DAuth unique?
The decentralized approach addresses many of the problems associated with centralized authentication solutions such as OAuth, SMS, and email which are widely used in Web 3.0 and are continuously damaging the ecosystem decentralization and the users' data security.
With DAuth, all dApps offering Web2-style authentication can become permissionless, eliminating any risk of denying service to a specific user.
DAuth uses a hybrid ZK technologies to provide a trustless authentication. This technology, when applying ZK to Web2 authentication, reduces the average authentication time to within 1 second. This satisfies the user's need for real-time response.
During the entire verification process, the user's account is invisible to the DAuth network. This means that users can authenticate their social accounts without revealing their identities. Moreover, DApps can send Emails and SMS messages to their subscribed users while keeping the user's email addresses and phone numbers private at the same time, giving the users greater control over their personal data and enhancing their privacy.
The DAuth protocol is compatible with all authentication methods such as OAuth, TOTP, SMTP, and SMS protocols, allowing developers to flexibly customize their authentication processes.
Last updated